From the CEO’s Desk: Implementing secure DevOps to innovate with confidence

Posted By
Chaitanya Jawale
Security was one of the most talked about terms in 2017, and some of the events such as Equifax, WannaCry, Bad Rabbit, and the Yahoo Bombshell of 2013 exposed the vulnerability of the current IT systems in place. Although most of these events were planned attacks rather than accidents, failure of the security measures taken resulted in the leaking data of millions of individuals and affecting companies with millions of dollars. On the positive side, this has fuelled the already initiated measures to integrate security teams and practices with development and operations teams. A combination of cultural changes more inclined towards the security side, practices that focus on augmenting the security of the overall environment, and tools that will automate the detection of any security concern and address them immediately is now the aim for the combined effort of security and DevOps movement together known as DevSecOps.
The level of contribution of the DevSecOps team may vary depending on the level of threat or complexity of the system, network, and application or the level of automation and the amount of manual effort that one needs to put in. Now, IT organizations want the SecOps personnel to concentrate more on the root cause analysis rather than only solving the problem. These causes can be categorized into four quadrants viz. simple, complicated, complex, and chaotic to better analyze the threats with a system called “Cynefin”. So now, your DevSecOps teams need to analyze these threats and their root cause and try to move the threats toward simpler from chaotic. This means disorders which are less impacting and can be easily overcome with simple and more automated solutions than more complex and manual ones. Because only finding and patching is not going to work hereon.
Previously most of the IT hardware and processes, except the thing that is interacting with the end user, was all in-house or on-premise and we had firewalls and monitoring tools to take care of the security. But then came the cloud and containerization evolution, and security has been on everyone’s mind since then. Considering the inherent financial and operational advantages, and scalability powers of cloud and containers, you can’t say no to these just because you have increased security concerns. So, what you do is address these security concerns, and that doesn’t only mean using tools and frameworks but a cultural shift where you plant the security seed at the very root of every process. The last time I talked about SecOps, the focus was more on tools and frameworks that you can leverage along with practices for container environment security. This time I will talk about the cultural aspects that can address the security concerns for your organization. What are the things which you as an organization need to do to bolster your security?
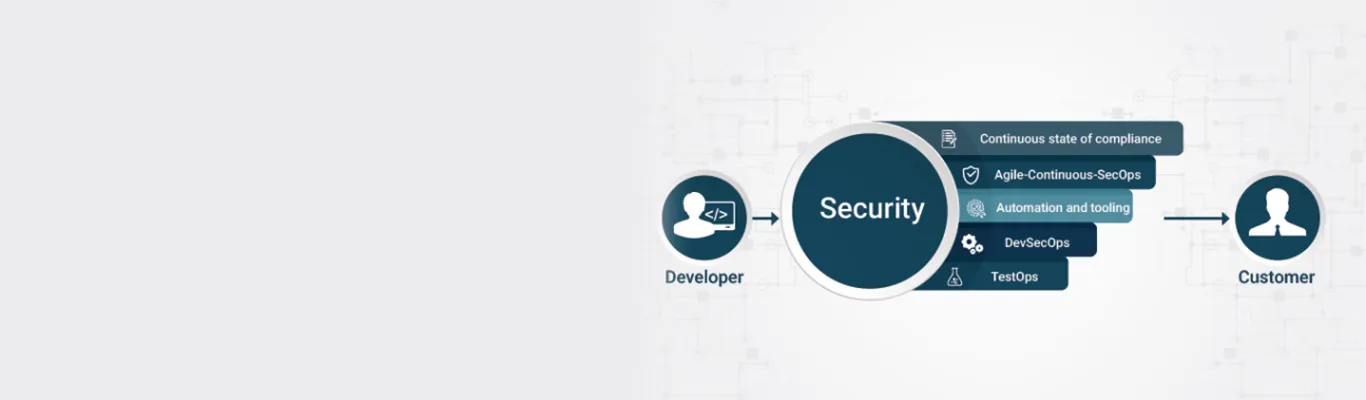
Here are a few of the cultural shifts and practices that will help strengthen security in your DevOps processes:
- Frequent and ad-hoc security checks: With frequent code releases, deployments and integrations, security checks can be included at every stage and in a timely manner to make sure your application and environment are free from any threat. In addition to this, ad-hoc security checks can also help in making sure security operations are capable enough to handle any attack.
- Bottom-up instead of top-down: Before SecOps, your security teams used tools to analyze the application as a whole, generate reports and then do the tuning like a top-down approach and this was time-consuming. But now, with continuous everything, you can’t afford to slow down everything for security reasons. And the security focus needs to be shifted to a bottom-up approach where the focus is on individual programs and components.
- Agile-Continuous-SecOps: Your SecOps practices should not affect the agile and continuous delivery processes but they should go hand-in-hand. Frequent security procedures and SecOps operations need to be in place for subsequent releases to cope with the agile and continuous methodologies.
- Revise your policies and practices for a continuous state of compliance, feedback, and visibility: Revising policies and practices to assess possible attack areas, tools and framework to use, possible areas that can be addressed in code itself, setting up security scanners, dynamic checks, uniform security policies, predefined, regular and real-time penetration testing, analysis of logs and reports to detect attackers as early as possible in the attack chain can bolster the defense with continuous feedback and continuous visibility. When a new code is created or changes are made to existing code, a system should be in place that will make sure compliance in real-time and generate reports and audits.
- Automation and tooling: Proper automation using tools and DevOps practices can help in automated security responses to possible threats reducing human intervention, and automated tests and dependency checks at every stage of the DevOps pipeline will make sure the application development process is free from any threat.
- SecOps and DevOps: Training your Dev and Ops teams to collaborate with the Sec team, tools, and practices can help in reducing the frequency of attacks with faster delivery of emergency patches.
- TestOps for security: I have mentioned many times that your testing teams have much bigger roles to play in terms of security now than ever. TestOps teams can check for vulnerabilities at every stage, right from the beginning of idea generation to post-deployment. Vulnerability testing should be made mandatory, along with functional and performance testing.
- The earlier, the better: Security considerations should be brought into the picture from the very beginning of conceptualization of the application and code design.
- Not only infrastructure: Security is normally associated with securing the infrastructure, but this is not the case now as most of us have minimal infrastructure in-house. So, the IaaS providers should focus on bringing their own security, monitoring, and analytical tools. And you, as the end users, can concentrate more on integrating these at the code design level.
Your age-old security practices are not going to stand against the dynamic changes and the more dynamic security threats to your IT environments. You need to combine the traditional security practices with the more dynamic SecOps practices, which can be fraught at the very beginning of planning and development processes. We don’t need to skedaddle old practices but, in fact, combine them with the new tools frameworks and, just like testing, shift the security to the left of the software development lifecycle. It is not as difficult as it looks, but it is certainly more important than it looks. Opcito can help you strike the equilibrium point between your DevOps and SecOps practices because, at the end of the day, the goal is simple: security.
Related Blogs