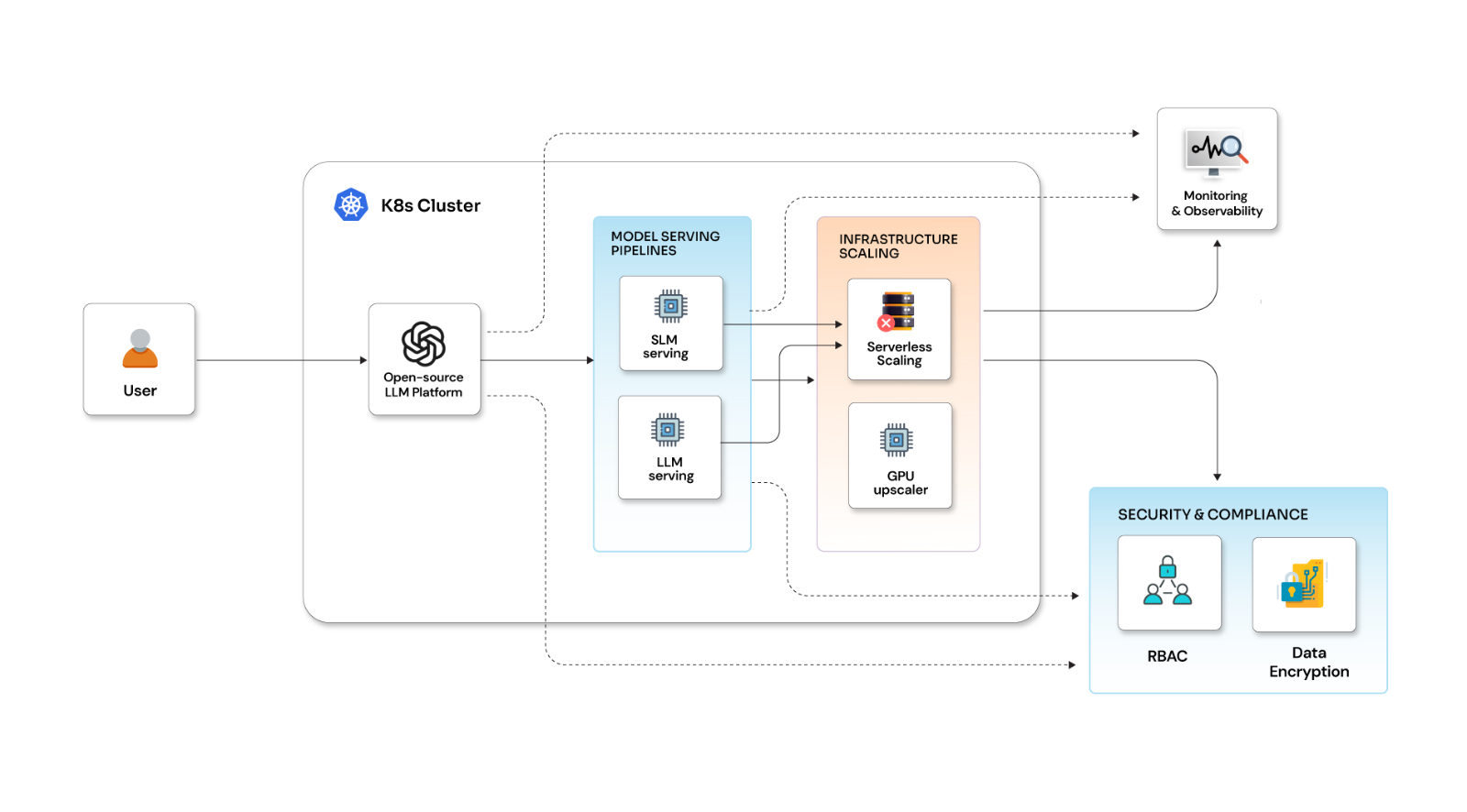
A technical deep dive into advanced Kubernetes Security Posture Management (KSPM)

Posted By
Kshitij Parbat

As Kubernetes continues to dominate cloud-native architectures, securing these dynamic environments demands more than superficial measures. From my years of working with teams that manage large-scale Kubernetes deployments, I've seen how overlooked configurations can cascade into major incidents. Kubernetes Security Posture Management (KSPM) maintains security hygiene in the face of constant change.
Building on our earlier discussions, which covered the foundational importance of KSPM in security and networking and explored real-world strategies, this guide delves into the technical details. Here, we'll dissect advanced KSPM techniques with code examples, risk analyses, and operational insights drawn from production environments.
Why KSPM is a strategic imperative for organizations
Fields like fintech or healthcare are always high-stakes, and KSPM goes beyond just following rules. It focuses on enabling innovation while avoiding serious risks. I've advised teams where lax posture led to downtime costing millions; conversely, robust KSPM has slashed incident response times by up to 80%. Let's break down the core pillars.
Achieving full cluster visibility
Visibility is the first step. Without knowing what workloads exist, what privileges they have, and which images are deployed, security is impossible to enforce. Tools like kube-state-metrics expose critical data, allowing you to query everything from pod statuses to RBAC bindings.
Consider a Prometheus query to monitor privileged pods across your cluster:
sum by (namespace) (kube_pod_spec_security_context_privileged == 1)
This metric indicates the number of pods running in privileged mode, organized by namespace. In practice, I've used similar queries to baseline security postures during audits, often uncovering 20-30% more risky configurations than manual reviews. By integrating this into Grafana dashboards, teams gain real-time insights, reducing blind spots that attackers exploit.
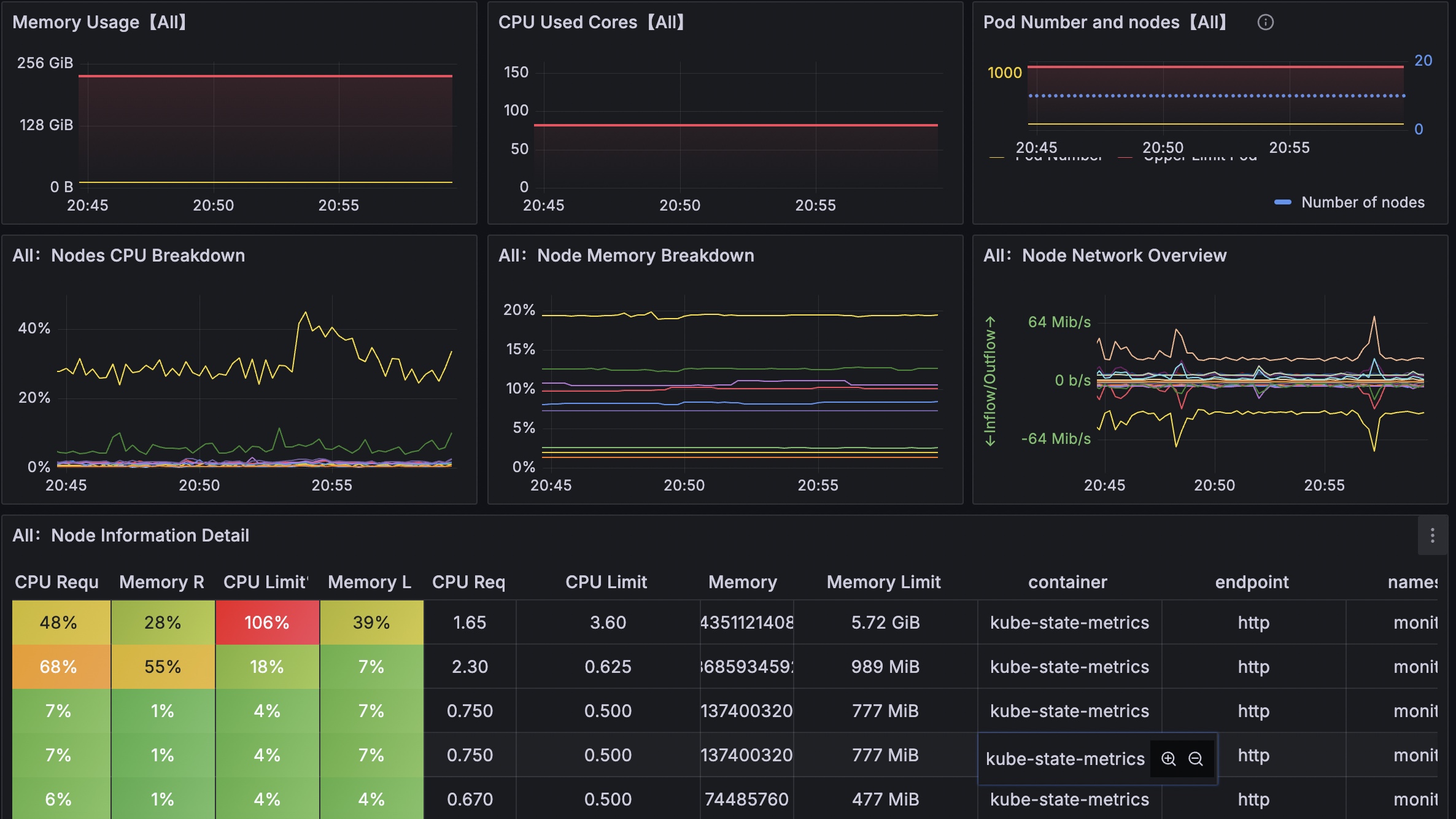
Best practice: Set up alerting thresholds, for example, to alert if privileged pods exceed 5% of total workloads. This not only flags anomalies but also tracks improvement metrics over time, such as a 50% reduction in risky pods following policy enforcement.
Enforcing policies for compliance and risk mitigation
Policies define your security boundaries. Without automation, they're just guidelines. In my experience, embedding policies via admission controllers prevents drift, ensuring compliance with standards like CIS Benchmarks or NIST SP 800-190.
My insight: Treat policy enforcement as code. Version control your policies in Git and integrate them into CI/CD for shift-left security. This approach has helped teams I've mentored deploy 2-3x faster while maintaining zero-tolerance for violations.
Our CI/CD services help integrate continuous security checks like Trivy into pipelines for faster, safer releases.
Leveraging automated remediation and observability
Detection without action is futile. Automated remediation closes the loop, turning alerts into fixes. Observability, powered by tools like Prometheus and the ELK Stack, provides the metrics to measure effectiveness, such as mean time to remediate (MTTR), dropping from hours to minutes.
Real-world example: In a multi-tenant setup, we automated namespace quarantines for non-compliant workloads, cutting exposure windows by 90%. Metrics such as violation rates per deployment cycle become key performance indicators of security maturity.
Detecting and remediating RBAC misconfigurations
RBAC (Role-Based Access Control) is Kubernetes' gatekeeper, but misconfigurations are rampant—I've seen them in 70% of audited clusters, often leading to privilege escalation.
Understanding the risks of over-permissive roles
Overly broad permissions invite trouble. Here's a risky example:
apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: namespace: default name: pod-wildcard-admin rules: apiGroups: [""] # "" indicates the core API group resources: ["pods"] verbs: [""] # "" gives all permissions
Risk: This allows any bound user or service account to create, delete, or exec into pods, potentially exposing secrets or enabling lateral movement. In a breach scenario, an attacker could pivot to critical services, violating principles like least privilege.
Impact: Compliance failures (e.g., SOC 2) and data leaks. I've encountered cases where this led to unauthorized access, resolved only after forensic analysis revealed the RBAC flaw.
Implementing least-privilege RBAC
Refine roles to minimize exposure:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: default
name: pod-reader
rules:
apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"] # Specific, read-only permissions
{code}
Bind this to a RoleBinding or ClusterRoleBinding as needed. To audit, use kubectl auth can-i --list to simulate access and identify over-permissions.
Best practices for RBAC management
- Audit Regularly: Run tools like rbac-tool weekly to visualize and prune roles. Track metrics like the average number of verbs per role. Aim for under 5.
- Namespace Scoping: Limit roles to specific namespaces to contain blasts.
- Documentation and Reviews: Require peer reviews for RBAC changes; document justifications for exceptions.
- Real-world insight: In a 500-node cluster, enforcing least privilege reduced attack surface by 60%, measured via vulnerability scans showing fewer exploitable paths.
Enforcing pod security with Policy-as-Code
Kubernetes won't stop you from deploying an insecure workload by default. You need a policy enforcement engine to act as a security guard for your cluster's API. This is where tools like OPA Gatekeeper and Kyverno come in. They are admission controllers that check every request to the Kubernetes API and block any that violate your security rules.
Why Use a Policy Engine?
- Consistency: Apply the same security rules across all your clusters.
- Prevention: Stop security issues before they are deployed, not after.
- Customization: Define fine-grained security rules tailored to your organization's needs.
Blocking Privileged Pods with Kyverno
While OPA Gatekeeper is powerful, its Rego language can be complex. Kyverno is a popular alternative that uses simple YAML to define policies, making it much easier to get started.
Here’s a Kyverno policy that blocks any new pods from running in privileged mode:
apiVersion: kyverno.io/v1 kind: ClusterPolicy metadata: name: disallow-privileged-containers spec: validationFailureAction: Enforce # Block requests that violate the policy background: true rules: name: validate-privileged-containers match: any: resources: kinds: Pod validate: message: "Running privileged containers is not allowed." pattern: spec: =(containers): =(securityContext): =(privileged): "false"
This policy is easy to read and enforce. When a user tries to create a privileged pod, the API server will reject it with the custom message, giving them instant feedback.
Continuous vulnerability scanning with Trivy
A secure posture also means ensuring your container images are free of known vulnerabilities (CVEs). Trivy is a fantastic open-source scanner that integrates directly into your CI/CD pipeline, acting as a security gate.
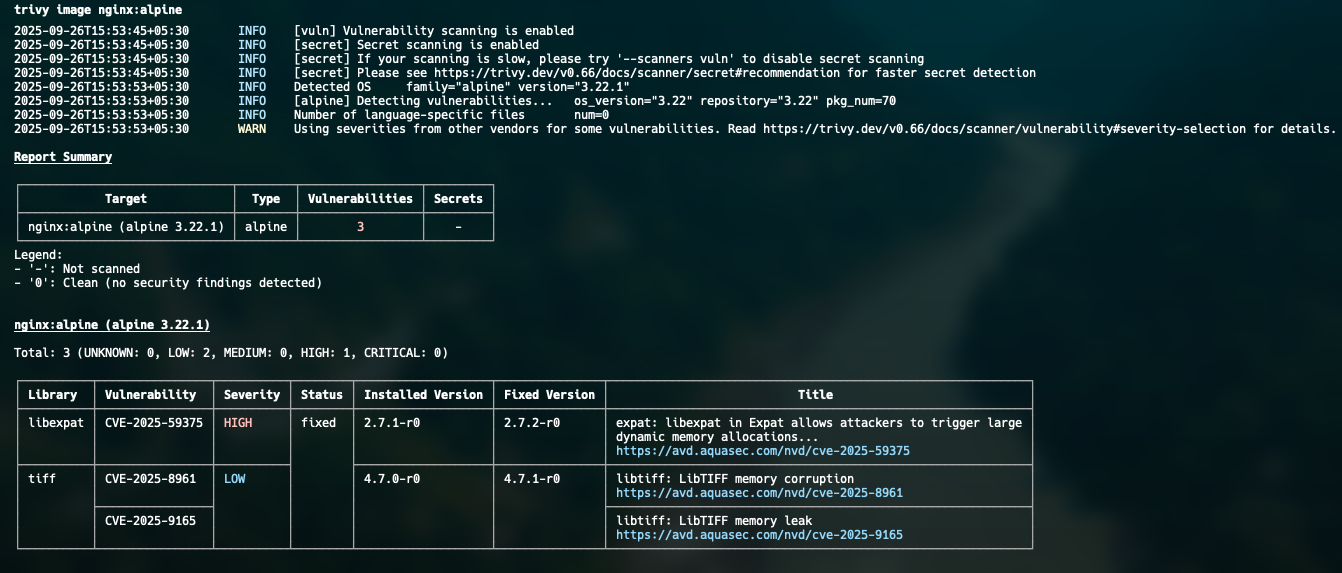
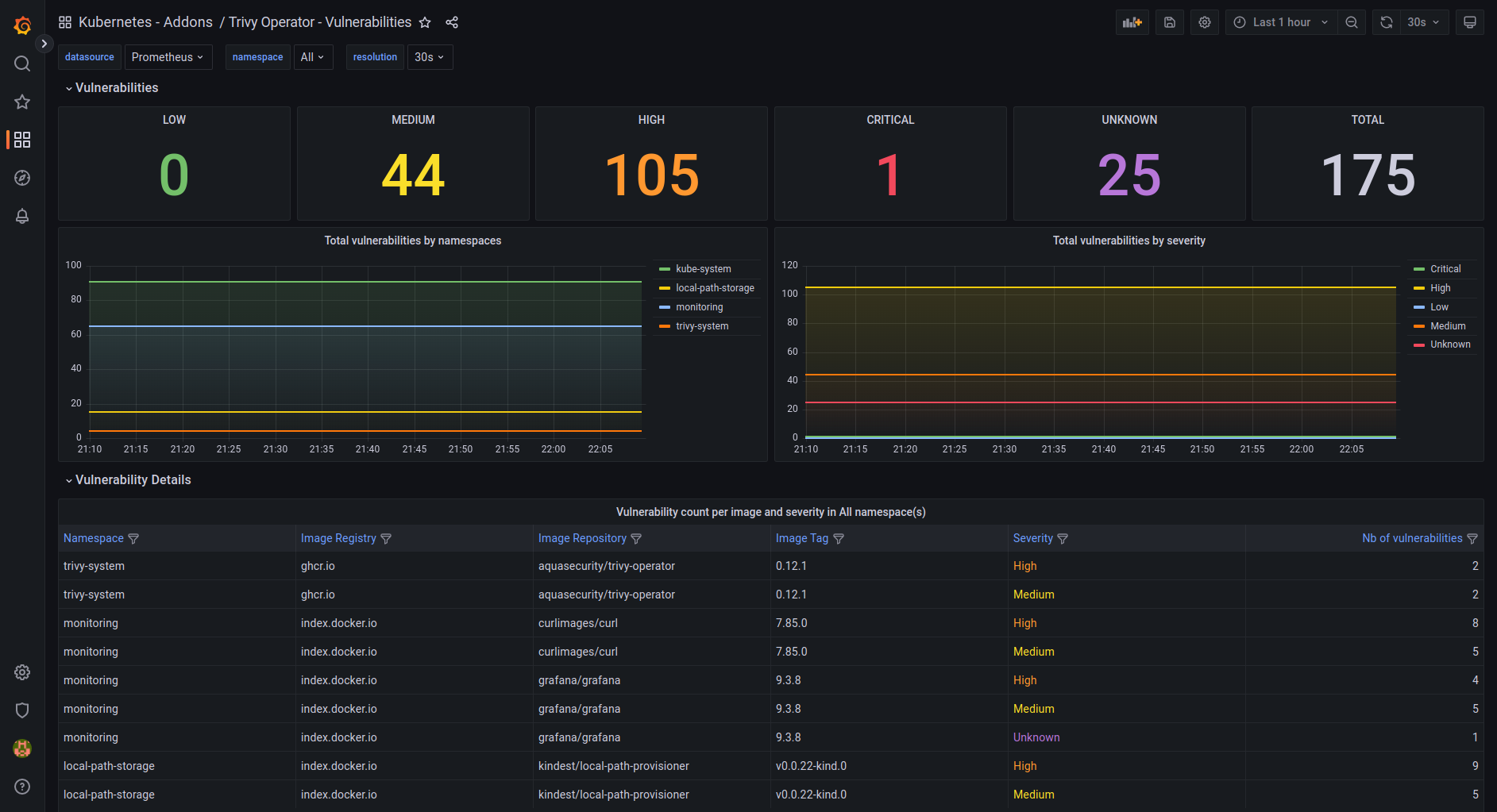
Integrating Trivy into GitHub actions
You can easily add Trivy to a GitHub Actions workflow to scan every new image you build. The workflow will fail the build if any high or critical severity vulnerabilities are found.
name: Build and Scan Docker Image
on:
push:
branches: [ "main" ]
jobs:
build-and-scan:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Build an image from Dockerfile
run: |
docker build -t myapp:${{ github.sha }} .
- name: Run Trivy vulnerability scanner
uses: aquasec/trivy-action@v0.22.0
with:
image-ref: 'myapp:${{ github.sha }}'
format: 'table'
exit-code: '1' # Fail the build if vulnerabilities are found
ignore-unfixed: true
vuln-type: 'os,library'
severity: 'CRITICAL,HIGH'
This "shift-left" approach catches security issues early in the development process, saving time and reducing risk.
Best practices for Trivy workflows
- Track vulnerability metrics: Log vulnerability counts per image; target fewer than five high-severity issues per release.
- Automated remediation: Use tools like Dependabot to auto-update vulnerable base images and dependencies.
- Shift left: Run Trivy scans early in development, not just at deployment, to reduce rework and risk.
Automating remediation for policy violations
Detection is great, but automatically fixing issues is even better. While admission controllers prevent new misconfigurations, you still need a way to handle anything that already exists in the cluster.
Instead of a disruptive approach like automatically deleting pods, a safer, more advanced method is to label non-compliant resources for review. This allows you to flag issues without causing an outage.
Here's a Kubernetes CronJob that runs every hour. It finds privileged pods and applies a security-violation=true label to them.
apiVersion: batch/v1
kind: CronJob
metadata:
name: label-privileged-pods
spec:
schedule: "0 * * * " # Every hour
jobTemplate:
spec:
template:
spec:
serviceAccountName: pod-labeler-sa # Needs permissions to get and patch pods
containers:
- name: kubectl-labeler
image: bitnami/kubectl:latest
command:
- /bin/sh
- -c
- |
kubectl get pods --all-namespaces -o jsonpath='{range .items[?(@.spec.containers[].securityContext.privileged==true)]}{.metadata.namespace}{" "}{.metadata.name}{"\n"}{end}' | while read namespace pod; do kubectl label pod $pod -n $namespace security-violation=true --overwrite; done
restartPolicy: OnFailure
Once labeled, you can:
- Alert: Set up alerts to notify the resource owner.
- Visualize: Create a dashboard showing all resources with this label.
- Quarantine: Use network policies to restrict network access for labeled pods.
This approach gives teams time to fix the underlying issue while still tracking and containing the risk.
Workflow best practices
- Combine with Webhooks: Use for immediate fixes, CronJobs for periodic sweeps.
- Monitoring: Track remediations via kube_job_status_failed.
- Insight: In a production rollout, this reduced MTTR by 70%, preventing escalations.
Advanced monitoring and observability in KSPM
Monitoring turns data into decisions.
Key Prometheus queries for security posture
Track RBAC changes:
sum(changes(kube_rbac_authorization_v1_rolebinding[5m]))
For pod security:
sum(kube_pod_container_status_running{securityContext_privileged="true"})
Integrate with alerts: Notify on spikes.
Observability best practices
- Dashboards: Custom Grafana panels for execs (high-level risks) and engineers (detailed violations).
- Integration: Pipe to SIEM for correlation.
- Metrics: Aim for 99% policy compliance, measured weekly.
Integrating DevOps and SRE for robust KSPM
At Opcito, our DevOps and SRE services embed KSPM into your pipelines, ensuring security scales with growth. We've helped clients automate compliance across 100+ clusters, reducing risks while accelerating releases.
Ensuring continuous enforcement
Align pipelines with policies via GitOps tools like ArgoCD.
Scaling policies across clusters
Use Federation for unified management.
Benefits for leadership
- Faster, safer deployments.
- Quantifiable risk reduction (e.g., 40% fewer incidents).
- Audit-ready postures.
Learn more about how our DevOps Security offerings strengthen Kubernetes environments with proactive risk management.
Closing thoughts
Mastering KSPM demands ongoing commitment, but the payoff of resilient and scalable Kubernetes is immense. At Opcito, we're partners in this journey, offering tailored expertise to fortify your clusters. Reach out at contact@opcito.com to discuss how we can elevate your security posture.